What is Zero Trust?
NIST 800-207 defines Zero Trust as providing:
“...a collection of concepts and ideas designed to minimize uncertainty in enforcing accurate, least privilege per-request access decisions in information systems and services in the face of a network viewed as compromised."
“This definition focuses on the crux of the issue, which is the goal to prevent unauthorized access to data and services coupled with making the access control enforcement as granular as possible.”
Koverse applies Zero Trust principles to data at rest by enabling data owners to reduce the granularity of privilege to the record or sub-record level, and by performing access decisions for every data access request regardless of previously successful requests. This allows data owners to shrink implicit trust zones down to the record and sub-record level, and for changes in data access policies to be affected in real time. It also means that organizations can make access control decisions based on data, regardless of network location.
Further, Koverse allows data to be protected using both role-based access control (RBAC) and attribute-based access control (ABAC).
In the Zero Trust Maturity Model, “data” is one of the pillars. Koverse goes beyond even the Optimal requirements outlined in this model for data at rest.
"Agency data should be protected on devices, in applications, and networks. Agencies should inventory, categorize, and label data, protect data at rest and in transit, and deploy mechanisms for detection data exfiltration."
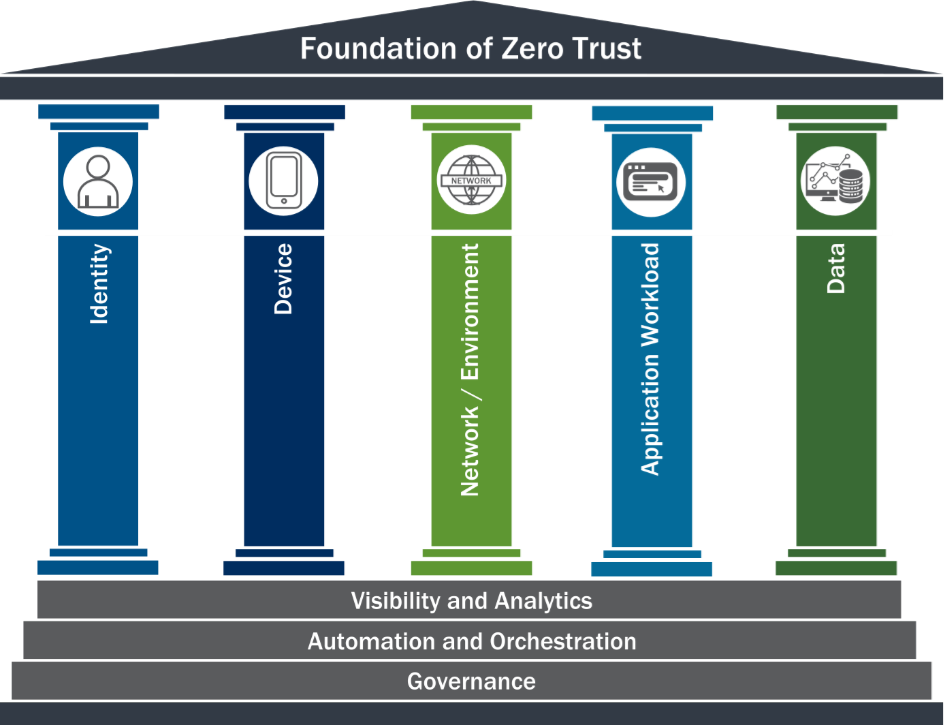
We’ll review how Koverse fulfills or exceeds the optimal requirements for the data pillar.
Inventory Management - “Agency continuously inventories data with robust tagging and tracking. Agency augments categorization with machine learning models.”
Koverse provides a crucial data tagging capability to data, allowing data sets, columns, individual records and sub-records to be tagged with security labels that define read access requirements.
Custom machine learning models can be included in this data tagging process, especially when tags do not already exist in the data or when humans have not yet tagged the data.
Access Determination - “Agency’s access to data is dynamic, supporting just- in-time and just-enough principles, and continual risk-based determinations.”
See the discussion of supported zero-trust tenets above, and the specifics of ABAC implementation in the next section for how Koverse allows data owners to minimize implicit trust zones and address the dynamic nature of changes in security policies.
Encryption - “Agency encrypts all data at rest.”
All data stored by Koverse is encrypted. Koverse provides fine-grained access controls over data that would be infeasible to attempt to implement using encryption alone. The combination of encryption and Koverse’s RBAC and ABAC capabilities ensures data is protected from unauthorized access and physical theft.
Visibility and Analytics Capability - “Agency’s data are inventoried and can always be accounted for. Agency logs and analyzes all access events for suspicious behaviors. Agencies perform analytics on encrypted data. “
Koverse provides extensive audit logging of all actions occurring within the data layer. Koverse is also actively being used along with homomorphic encryption technology providers to enable secure analytics of encrypted data.
Automation and Orchestration Capability - “Agency automatically enforces strict access controls for high-value data. All high-value data is backed up regardless of its storage location. Data inventories are automatically updated.”
Koverse provides RBAC and ABAC capabilities to control access for high-value data. Koverse is also used to make data highly available by replicating data automatically across storage devices.
It is common for Koverse to be used to continuously ingest new data, so datasets are automatically kept up to date.
Governance Capability - “Agency automatically always enforces data protections required by policy. Data categorization and data access authorizations are defined using a fully unified approach that integrates data, independent of source.”
Koverse provides a unique ability to physically co-locate, while logically isolating, data from any source, whether structured or unstructured. This enables organizations to implement a single unified set of security policies to control that data, independent of source or type.